As part of the current Software application development approach, Security is one of the concerns we should take as serious. The Internet is growing with threats. We must secure our application from those threats in all the possible ways. If we have some structured approach like DevOps for Software development, it will be easy to implement in the existing process. In the modern world, we have DevSecOps to implement security in the Software Development process in a structured way. This article will give you some Approaches to Automate Security Testing in CICD Pipelines.
Table of Contents
Security Testing Methodologies
Before going into the Approaches, Let’s discuss some Approaches and tools that help to implement those.
- SAST (Static Analysis)
- DAST (Dynamic Analysis Fuzzing)
- IAST
- SCA
- Secret Detection
- Licensing Analysis
Static Application Security Testing (SAST)
SAST is the Security testing methodology to analyze the codebase and design the rulesets that is to indicate the security vulnerabilities especially in nonrunning state of the application. This make SAST Whitebox testing.
Some Available Tools to implement SAST

Dynamic Application Security Testing (DAST)
DAST is a Blackbox testing methodology for software Security to analyze the application when it runs and tries to hack from outside like a hacker. DAST is mostly designed for Web-based application especially via HTTP connections.
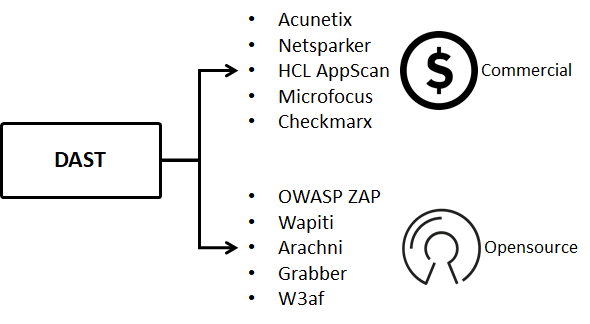
Tools to implement DAST
Interactive Application Security Testing (IAST)
IAST is Whitebox testing and it will run while the application is running. This means Security testing will try to find the vulnerabilities when the application is getting interacted by Automated testing or Human Tester or by any means of Interaction to application.
Tools to implement IAST

Software Composition Analysis (SCA)
SCA is the process of automating the insight of open source software (OSS) use to know and understand the risk management, security and license compliance.
Some Available Tools to implement SCA

Secret Detection (SD)
Secret Detection is the set of processes and rulesets to detect sensitive information, like passwords, authentication tokens, and private keys are unintentionally leaked as part of the source code or antifactory repository content.
Tools to implement Secret Detection

License Analysis
License Analysis is an approach to detect license and it will check whether its complies with the SLA and other legal instrument governing the usage or redistribution of copyright-protected software, modules, and packages used in the Software development
List of tools to implement License Management

Implementing security in CICD Pipeline
Now, Let’s get into the Approaches to Automate Security Testing in CICD Pipelines. So, Let’s assume the following CICD pipeline or workflow that explains from developer to production lifecycle. When the process is in Developer’s environment say pre-commit or in IDE, we should consider implementing the security approaches offline. Similarly, for all the stages of the CICD pipeline. So, In this segment, we will discuss how the above methodologies and approaches are been used in the CICD pipeline.

At Development Environment
As mentioned in the above image, when the CICD process is in the Development stage or in the pre-commit stage, we are going to scan the code before getting into the SCM. Here, the meaning of the scanning is to check any vulnerability as per the threat modeling and peer code review.
At Commit
In the Commit phase, Source code will be moved to SCM and Security testing will be done in this phase. So, this testing will be triggered when the source code will be checked-in into the SCM. Here, with the help of Incremental SAST, Compile and build with Security Ruleset will be executed with automated security testing.
At Build
The Build phase is where the Continuous Integration process ends. Here, SAST will be configured with more Rulesets. SCA will be configured to identify external packages and OSS risks. Along with this, Configuration of Automated and risk-based tests will be carried out and alert on high risk will be notified to the respective team.
At Test
At the normal Testing phase, SAST will be configured with even more deeper Rulesets outlined with OWASP top 10. Along with it IAST and DAST will be configured to identify the Security threats which is more complex to identify in Whitebox testing. Here, Fuzz testing will also be taking place. This is the best place to test our configurations too.
At Deployment
Pre and Post-Deployment Security testing will be takes place to identify threats like Vulnerability issue with configuration management system and application runtime platforms like servers. This will help us to capture the vulnerability before and after the deployment takes place.
At Production
Security threat is real even when the application is in production. Because time being hackers and attackers will come up with new threats and malware that should be identified and reacted immediately. Hence to identify the threat and breach at production, scheduled PEN test, and Continuous Monitoring is needed.
Conclusion
Growing technology creates the opportunity to achieve advanced features and quick and quality software. Also, it is coming up with Security threats and Vulnerability which is a serious problem the current generation should take care. If The Software Development platform is outdated, Security testing framework implementation is always challenging. DevOps will give you the best place to create opportunity to implement the structured Security testing approaches. Hope this Approaches to Automate Security Testing in CICD Pipelines will give you the fare idea of designing security testing at CICD pipeline. Stay tuned and subscribe DigitalVarys for more articles and study materials on DevOps, Agile, DevSecOps and App Development.

Experienced DevSecOps Practitioner, Tech Blogger, Expertise in Designing Solutions in Public and Private Cloud. Opensource Community Contributor.






